A suspected Chinese hacking group has been linked to the zero-day exploitation of a medium-severity security flaw (CVE-2022-41328) in Fortinet’s FortiOS operating system, now patched. Mandiant, a leading American cybersecurity firm, attributes this activity to a broader campaign aimed at deploying backdoors on Fortinet and VMware solutions, granting persistent access to victim networks.
The cyber espionage operation, tracked as UNC3886 by Mandiant, is characterized as a China-affiliated threat actor. The group exhibits advanced on-network capabilities and employs specialized tools in their campaigns, particularly targeting firewall and virtualization technologies lacking EDR support. Their expertise in manipulating firewall firmware and exploiting zero-day vulnerabilities highlights their deep understanding of these technologies.
Previously, UNC3886 was connected to intrusions targeting VMware ESXi and Linux vCenter servers in a hyperjacking campaign deploying backdoors like VIRTUALPITA and VIRTUALPIE. The latest disclosure follows Fortinet’s announcement of government entities and large organizations being targeted by an unidentified actor exploiting the FortiOS zero-day bug, resulting in data loss and file corruption.
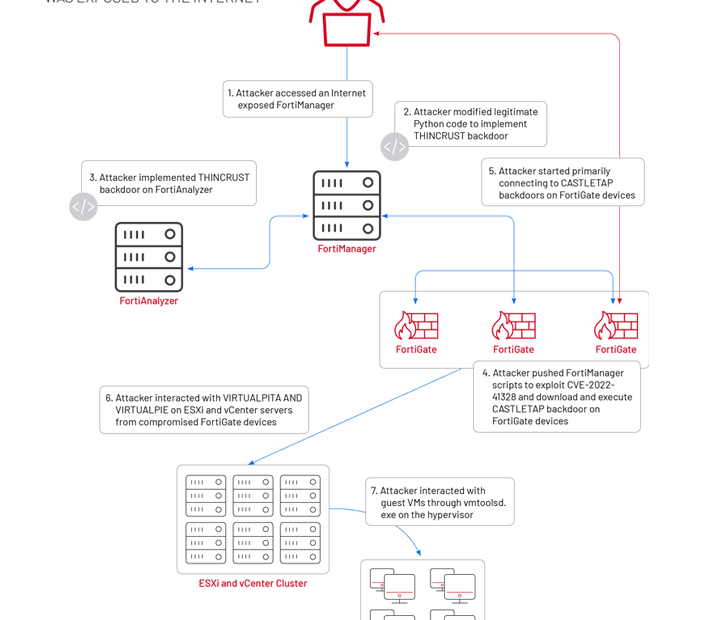
Mandiant reports that UNC3886 targeted Fortinet’s FortiGate, FortiManager, and FortiAnalyzer appliances to deploy implants such as THINCRUST and CASTLETAP. This was possible due to the exposure of the FortiManager device to the internet. THINCRUST, a Python backdoor, enables arbitrary command execution and file access, which is used to weaponize the FortiOS path traversal vulnerability, overwrite files, and modify firmware images.
The added payload CASTLETAP communicates with an attacker-controlled server to receive instructions for running commands, fetching payloads, and exfiltrating data. Once deployed, UNC3886 connects to ESXi and vCenter machines, establishing persistence using VIRTUALPITA and VIRTUALPIE for continued access to hypervisors and guest machines.
In cases where FortiManager devices have internet access restrictions, UNC3886 pivots from a compromised FortiGate firewall using CASTLETAP to deploy a reverse shell backdoor called REPTILE. The group also employs a network traffic redirection utility, TABLEFLIP, to connect directly to the FortiManager device, bypassing access control list (ACL) rules.
Chinese threat actors have a history of targeting networking equipment to distribute custom malware, exploiting vulnerabilities in Fortinet and SonicWall devices. Rapid7 reports an increase in exploit development and deployment speed, with 28 vulnerabilities exploited within a week of public disclosure—a 12% increase over 2021 and an 87% increase over 2020.
China-aligned hacking groups have become notably skilled at exploiting zero-day vulnerabilities and deploying custom malware to steal credentials and maintain long-term access to target networks. Mandiant’s findings underscore the need for organizations to be aware of advanced cyber espionage actors taking advantage of technologies without EDR support to persist and traverse target environments.
As cyber espionage groups like UNC3886 continue to adapt and exploit a wide range of technologies, it is crucial for organizations to prioritize comprehensive cybersecurity measures to protect their networks and assets. Staying informed about emerging threats, adopting best practices, and investing in robust security solutions can help reduce exposure to risk.
To defend against threat actors like UNC3886, organizations should:
- Regularly update and patch software and hardware to address known vulnerabilities and zero-day exploits in a timely manner.
- Implement strong access controls, including multi-factor authentication (MFA) and least privilege policies, to prevent unauthorized access.
- Deploy intrusion detection and prevention systems (IDPS) to monitor network traffic, detect potential threats, and respond effectively.
- Educate employees on cybersecurity best practices, emphasizing the risks associated with phishing attacks, social engineering, and malware.
- Utilize endpoint detection and response (EDR) solutions to identify and mitigate threats at the device level.
- Conduct routine security audits and assessments to identify and remediate vulnerabilities and gaps in the organization’s security posture.
- Develop and maintain a comprehensive incident response plan to guide organizations in the event of a security breach or cyber attack.
By staying vigilant and proactively addressing potential threats, organizations can strengthen their defenses against advanced cyber espionage actors like UNC3886. As these groups continue to exploit technologies without EDR support and other vulnerabilities, it is essential for organizations to invest in robust security measures to safeguard their networks and valuable assets.
In addition to the aforementioned measures, organizations should also consider implementing advanced security strategies to further fortify their defenses against sophisticated threat actors like UNC3886. Some of these strategies include:
- Adopting a zero-trust security model: By assuming that no user or device is trusted by default, a zero-trust approach requires continuous verification of user identities and device integrity before granting access to sensitive resources.
- Implementing threat intelligence sharing: Collaborating with other organizations and industry partners to share information about the latest threats, vulnerabilities, and best practices can help organizations stay ahead of emerging risks and develop effective countermeasures.
- Leveraging artificial intelligence (AI) and machine learning (ML) technologies: AI and ML-powered security solutions can help detect and respond to threats more efficiently and effectively by analyzing vast amounts of data and identifying patterns indicative of malicious activities.
- Utilizing security orchestration, automation, and response (SOAR) platforms: SOAR solutions can help streamline security operations by automating routine tasks and orchestrating incident response processes, allowing security teams to focus on higher-priority tasks and more complex threats.
- Conducting regular red team exercises and penetration testing: Simulating cyber attacks on an organization’s infrastructure can help identify vulnerabilities and weaknesses in its security defenses, enabling the organization to take corrective action before a real attack occurs.
- Establishing a strong security culture: Encouraging a culture of security awareness throughout the organization ensures that all employees understand their roles and responsibilities in maintaining cybersecurity and are equipped to recognize and respond to potential threats.
By integrating these advanced security strategies into their overall cybersecurity posture, organizations can further enhance their defenses against highly skilled and persistent threat actors like UNC3886. As the cyber threat landscape continues to evolve, a proactive and comprehensive approach to security is essential to protect valuable assets and maintain the integrity of critical systems and networks.