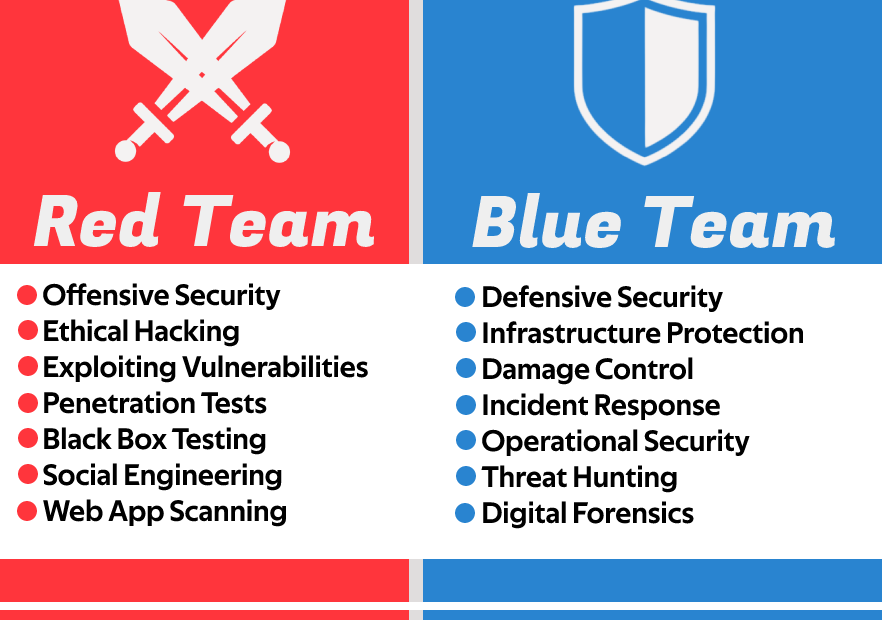
In the field of cybersecurity, organizations often use a combination of red and blue teams to improve their overall security posture. These teams play different roles in the cybersecurity ecosystem, with the red team acting as the attacker and the blue team as the defender. In this blog post, we will discuss the difference between a red and blue team in cybersecurity.
Red Team
A red team is a group of security professionals who simulate real-world attacks on an organization’s systems, networks, and applications. They do this to identify vulnerabilities and weaknesses in the organization’s security defenses. Red teams use a variety of tactics, techniques, and procedures to simulate attacks, including social engineering, phishing, and exploiting known vulnerabilities.
The goal of the red team is to uncover weaknesses that could be exploited by real attackers. They then report these weaknesses to the organization’s blue team, who can take steps to remediate them.
The red team operates under a set of rules of engagement (ROE) agreed upon with the organization. The ROE outlines what types of attacks are allowed and what is off-limits. This ensures that the red team’s activities do not cause any harm to the organization’s systems or data.
A blue team is a group of security professionals who defend an organization’s systems, networks, and applications against attacks. They use a variety of tools and techniques to monitor and defend against attacks, including intrusion detection and prevention systems (IDS/IPS), firewalls, and security information and event management (SIEM) systems.
The blue team’s goal is to identify and mitigate security vulnerabilities before they can be exploited by attackers. They work closely with the red team to understand the weaknesses identified by the red team and take steps to remediate them.
The blue team also monitors the organization’s systems and networks for signs of a breach. If a breach is detected, they take immediate action to contain and remediate it.
Differences Between Red and Blue Teams
The primary difference between red and blue teams is their role in the cybersecurity ecosystem. The red team plays the role of the attacker, while the blue team plays the role of the defender. The red team’s goal is to identify vulnerabilities and weaknesses in the organization’s security defenses, while the blue team’s goal is to defend against attacks and mitigate vulnerabilities.
Another key difference is the tools and techniques used by each team. The red team uses a wide range of attack methods, including social engineering, phishing, and exploiting known vulnerabilities. They may also use custom malware or other attack tools to simulate real-world attacks.
The blue team, on the other hand, uses a range of defensive tools and techniques to monitor and defend against attacks. They use tools like IDS/IPS, firewalls, and SIEM systems to detect and respond to attacks.
Finally, the red team and blue team have different goals when it comes to reporting their findings. The red team reports vulnerabilities and weaknesses to the blue team, who then takes steps to remediate them. The blue team may also report their findings to senior management or other stakeholders to demonstrate the effectiveness of their security program.
Conclusion
In conclusion, the red team and blue team play critical roles in an organization’s cybersecurity program. The red team simulates real-world attacks to identify vulnerabilities and weaknesses, while the blue team defends against attacks and mitigates vulnerabilities. By working together, these teams can improve an organization’s overall security posture and protect against cyber threats.
It’s important for organizations to have both a red team and blue team in place to ensure that their security defenses are strong and effective. If you’re interested in improving your organization’s cybersecurity program, consider hiring a team of skilled professionals to conduct a red team/blue team exercise. This will help you identify vulnerabilities and weaknesses in your security defenses and take steps to remediate them before an attacker can exploit them.